ANTI-PHISHING ADVICE

We recently had a customer report being tricked into sending money to the wrong place. We have seen an increase in the amount of this kind of activity since the pandemic began. I think the hackers realize that in the current environment companies are readjusting to a remote workforce. They are exploiting gaps in communications because of the loss of in personal interaction. This is creating new targets of opportunity.
Companies and employees (through both business and personal activity) are producing a wealth of information for hackers to gather every day. They then use this knowledge to craft targeted attacks against employees.
How can companies protect themselves? We have examined several of these attacks and they are very well crafted. Here are some of our suggestions to protect yourself.
- Educate your employees! People tend to be the weakest link in any security system. You should have routine training in security and loss prevention for all employees, especially for those in the C suite (prime targets).
- Treat all email as insecure. Hackers often impersonate a trusted associate by collecting information about the company and employees, then crafting an email, when opened launches the attack. A common hack sets up a forwarding rule that sends a copy of your email to the attacker’s email address. Now the attacker learns more about your daily operation which they use for further attacks.
- Have established procedures. Create procedures for any communications requesting a change in procedure (financial or otherwise) such as the following:
- Call the company / person in question using a previously known phone number. The call should preferably be made by someone who deals with the company / person in question on a regular basis so they can validate the contact. Verify the requested change. Ask for specific supporting information.
- Don’t click on links or call numbers provided in the email. These often activate the attack or direct you to a very authentic looking web site that collects more data or launches an attack.
- Don’t respond to the email via email until you’ve established that the request is legitimate. If the request is a hack, you will have confirmed the hacker’s information and advanced the attack.
- Never provide any passwords, account numbers, personal information, or other information via email. Each new piece of information is an additional weapon to be used against you.
- Be suspicious of any emails requiring urgent action. Hackers will try to trick you into hasty action before you have had a chance to think about it.
- Question any unsolicited or out of character communications. Why is John (who is a stockperson) asking for the accounts payable person’s name, phone number, or email? Why is my customer suddenly unable to accept checks when you can still scan or deposit via ATM? Why does my supplier suddenly have a new web address?
- Look for grammatical or spelling errors. Attacks are often initiated overseas and the attacker may lack the nuances of your local dialect. Check the writing style. If you have been corresponding with the sender in the past, you probably have a sense of their writing style.
These attacks often come when key people are sick or on vacation or when somebody new starts with the company. Attackers know a lot of people are working remotely these days and may not have access to the people or files that would help them deflect the attack.
Your IT department should be leading the effort to prevent these attacks, but each of us plays an important role in security. A chain is only as strong as its weakest link.
CREATING SECURE PASSWORDS
So how do I create secure passwords? My method is very simple yet generates very complex passwords. It starts with a number that you will never forget such as your social security number, a 10 or 7 digit phone number, the combination of 2 digit birthdays. For demonstration purposes I’ll use 123-4567. You will also need a starting character or number, I’ll use the letter “a”. Now all you need is a keyboard and the ability to count.
You will be forming your password by counting keys on your keyboard using only the 10 digit keys at the top and the lettered keys below. You count left to right, top to bottom.

So for my example my password starts with “a”. The first digit in my number is 1 so I count 1 key to the right of “a” and get “s”. My password is now “as”. My next digit is 2 so I count 2 keys to the right of “s” and get “f”. My password is now “asf”. Next is 3 so counting to the right I get “j” for a password of “asfj”. Next is 4, so I start counting 4 keys, when I get to the “l” key I wrap around and down to “z” ending on “x” for a password of “asfjx”. Next we do the 5 and end up on the “m” key giving us “asfjxm”. Now we do the 6 but since we are at the end of the letter keys, we wrap our count up to the starting point on the keyboard or the “1” key and continue counting to the “6” key giving us “asfjxm6”. Lastly we do the 7 and end up on the “e” key giving us a final password of “asfjxm6e”.
So you can see even using a simple number sequence can generate a very complex password. You can also change the direction of count and add capitalized / shifted characters to make it even more complex. When you combine this technique with using a password manager like LastPass you will have a very secure online environment. I’ll cover LastPass in my next installment.
If you want to try it, generate a password using “g” as your starting character and the number 201-977-2299. Hint: for 0 use the same key. Send us an email at support@benntech.net with your answer.
COMMON RAID LEVELS
RAID 1
RAID 1 consists of an exact copy (or mirror) of the data across two disks. The resulting data storage capacity is equal to the capacity of the smallest disk. This configuration is fault tolerant to the failure of one disk.
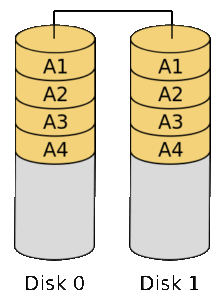 |
RAID 1RAID 1 consists of an exact copy (or mirror) of the data across two disks. The resulting data storage capacity is equal to the capacity of the smallest disk. This configuration is fault tolerant to the failure of one disk. |
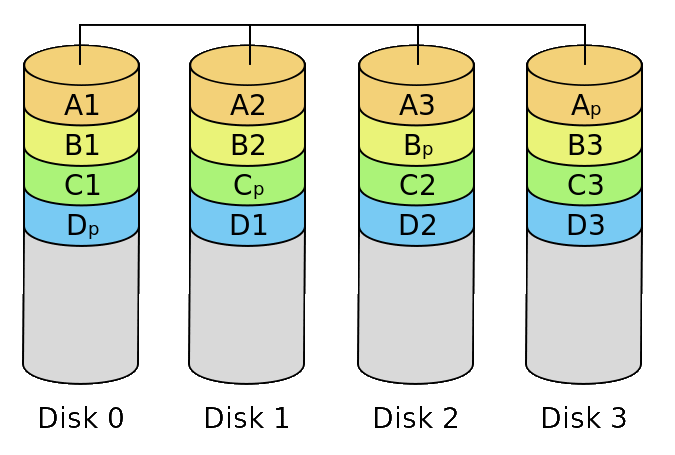 |
RAID 5RAID 5 consists of block-level striping with distributed parity (i.e parity information is distributed among the drives) across 3 or more disks. The resulting data storage capacity is equal to the capacity of all the disks added together minus one disk. This configuration is fault tolerant to the failure of one disk. Upon failure of a single drive, subsequent reads can be calculated from the distributed parity such that no data is lost. |
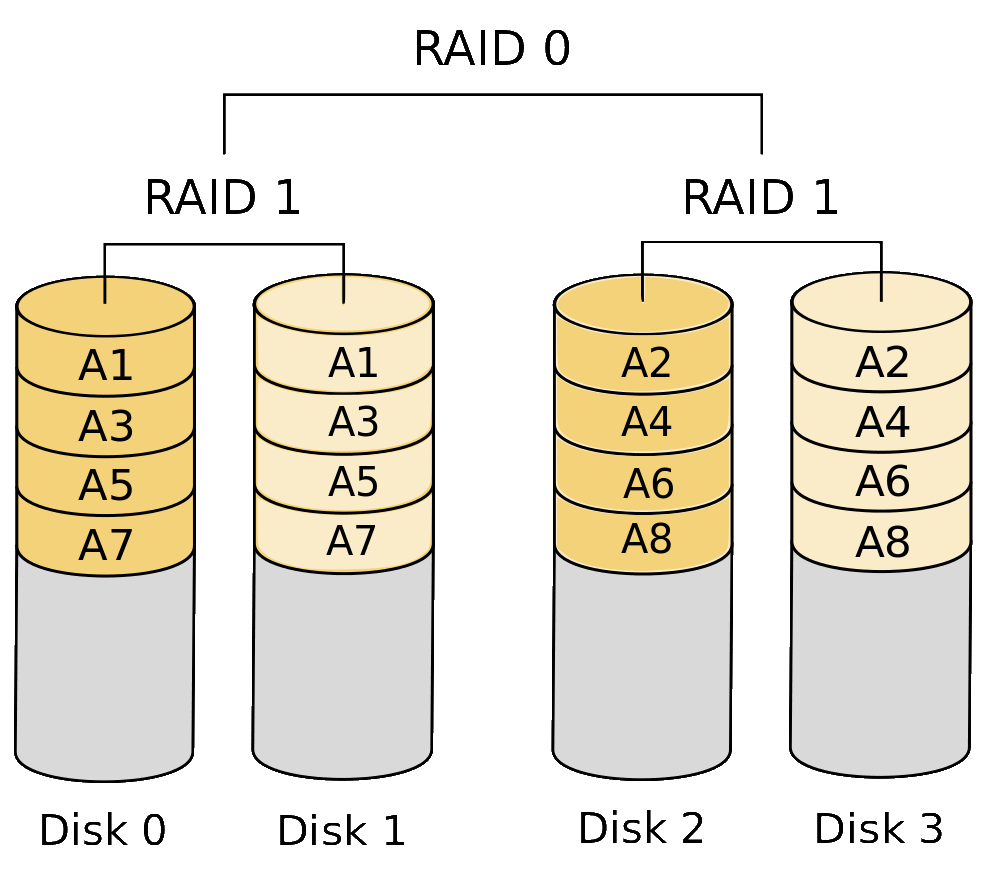 |
RAID 1+0 or RAID 10RAID 10 consists 2 mirror sets with data striped across the sets. The resulting data storage capacity is equal to the capacity of 1/2 of all the disks added together. This configuration is fault tolerant to the failure of two disks, one in each set. This configuration provides the best throughput of the RAID configurations shown here. |
